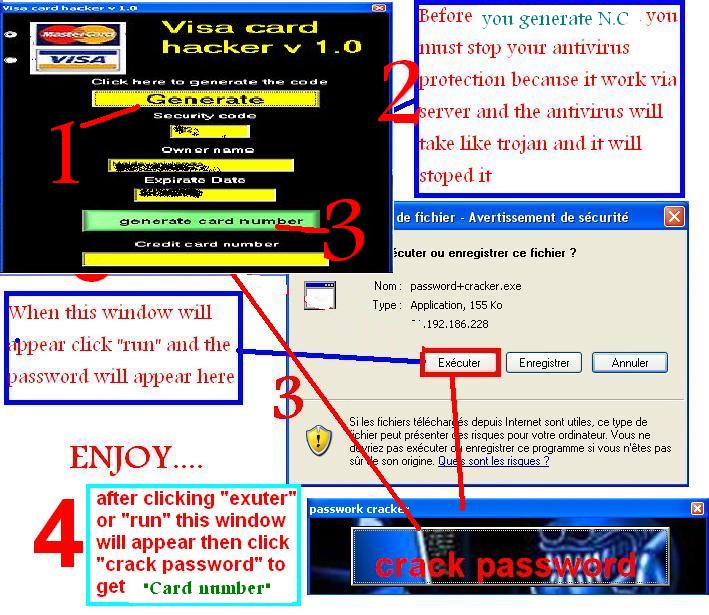
Hack Credit Card On Irc
XDA Developers was founded by developers, for developers. It is now a valuable resource for people who want to make the most of their mobile devices, from customizing the look and feel to adding new functionality. Find the best credit cards for travel hacking that will help you meet your goals. I love the Barclay AAdvantage, Chase Sapphire, and Chase Marriott Rewards cards. Apply for your new credit card before any big expenses (existing travel, electronics, auto repairs, taxes, etc) and put all of your recurring bills or other expenses onto the new card. During the first half of this year, 23 million credit cards were stolen worldwide. But what can a cyber criminal really do with a stolen credit card number? Experts say quite a lot.
It would be a small leap in some people's minds to go from stealing telephone connection time from a long distance company (by scanning through some accessnumbers and looking for valid ones) to using other acquired numbers (fromcarbons and stolen databases) to get free computer equipment and airlinetickets. This, apparently, was the draw of Credit Card Fraud, where stolencredit card numbers were used to charge thousands of dollars for whatevera budding felon decided they wanted to risk years of jail time for.
Even now, there's really no justification or warm glow associated with credit card fraud, but the following files promote the cavalier and on-the-edge approach to this second, deeper level of using 'codes'.
| Filename | Size | Description of the Textfile |
| ac1.txt | 6339 | Advanced Carding Techniques by The Disk Jockey |
| act_04.dj | 2365 | Advanced Carding Part 4: Motel Carding, by The Disk Jockey |
| advanced.txt | 9278 | Real Credit Card Fraud by Emergency Interript of Advanced Telecommunication Inc. |
| advcard3.txt | 2908 | The Disk Jockey Presents Advanced Carding III: Airline Carding |
| advcard4.txt | 2328 | The Disk Jockey Presents: Advanced Carding 4: Motel Carding |
| advcard6.txt | 2137 | The Disk Jockey Presents: Advanced Carding 6: Easier Drops |
| advcard7.txt | 2335 | The Disk Jockey Presents: Advanced Carding 7: The Other Side |
| advcard8.txt | 4679 | The Disk Jockey Presents: Advanced Carding 8: In-Person Carding |
| advcard9.txt | 1196 | The Disk Jockey Presents: Advanced Carding 9: Tips and Tricks |
| advcrd13.c_f | 2971 | The Disk Jockey Presents: Advanced Carding 13: The Student Card |
| afrocard.txt | 5495 | Mailboxing: How to Acquire Credit Cards |
| aicard.hac | 7630 | Careful Carding, by One-Eyed Willie |
| aicard.txt | 9219 | Careful Carding Techniques, by One Eyed Willie of AI |
| amex.txt | 9248 | How to Make Your Own Valid American Express Numbers in One Easy Step, by Saturday Knight |
| artcardi.txt | 24577 | The Art of Carding by DM 0verdose (May 4, 1991) |
| atms1.txt | 4096 | The Disk Jockey Presents: Scamming ATM's |
| bcformats.txt | 1291 | A List of Bank Card Formats |
| bgcard.txt | 8189 | Credit Carding Made Easy by David Lightman (March 28, 1985) |
| blockani.phk | 995 | How to Avoid Being Traced on BOC Calling Card Calls |
| callcard.hac | 1734 | Hacking Calling Cards by The Pyromaniac |
| callcard.phk | 1868 | Hacking Calling Cards, by The Pyromaniac |
| calling.phk | 28939 | Calling Card Secrets, transcribed from Bell Telephone |
| card-rl | 7196 | Carding in the 90's by The Knight of Renegade Legion (April 1991) |
| card.txt | 7986 | Some Basic Information about Credit Cards |
| card1.txt | 3767 | Credit Card Fraud made Easy, by Jimmy Z |
| card101.nap | 5248 | A NAPPA Profile on Carding, by Dr. Insanity |
| card101.txt | 6188 | The NAPPA Profile on Carding by Dr. Insanity of NAP/PA |
| card111.txt | 8844 | Carding, by Bloody Malice |
| card2.txt | 19054 | Some Thoughts and Instructions on Carding |
| card90rl.hac | 7060 | Carding in the 90's, by The Knight |
| card90rl.txt | 7388 | Carding In the 1990's by The Knight, April 1991 |
| cardass.txt | 13126 | How to Card Your Ass Off and Never Get Caught |
| cardbeg.txt | 4491 | Carding, an Overview |
| cardbig.txt | 2717 | Carding Hints from The Big Guy |
| cardchk.hac | 922 | Credit Check information |
| cardchk.txt | 1204 | Credit Card Checking, from the Tempest (July 5th, 1987) |
| cardfrau.txt | 3569 | How to Get a Lot of Stuff Free |
| cardfun.txt | 7501 | Credit Cards for Fun and Profit: A Treasure Island Presentation |
| cardhack.phk | 1830 | Nail Varnish and Card Calls |
| cardi90s.txt | 7113 | Carding in the 90's by The Knight of Renegade Legion (March 17, 1991) |
| cardin92.txt | 10506 | Cardin' 1992: Carding in the 90's by Special Ed (January 2, 1992) |
| cardindevpac.txt | 17876 | Carding, by Devpac |
| cardinfo.txt | 6656 | All About Carding, by Jack the Ripper of Thieve's Underground |
| cardinfy.txt | 5137 | Information on How to Card! |
| carding.basics | 17536 | The Fundamentals of Credit Card Engineering by Jumping Jack Flash (January 15, 1992) |
| carding.txt | 5347 | Carding Volume #1 by FX |
| carding1.txt | 4737 | The Basics of Carding by The Metallian of Metal Communications |
| carding2.doc | 4746 | The Basics of Carding, by the Metallian |
| carding2.txt | 29174 | Carding Volume II by The Metallian |
| carding3.txt | 35523 | Carding III: Higher Learning, by The Metallian of Neon Knights/Metal Communications |
| carding5.txt | 10491 | Carding Volume #1 by FX |
| cardnet.txt | 8632 | OTG Presents Cards and the Networks |
| cardread.hac | 30142 | Card Reading Public Station Requirements (Bellcore document) |
| cards!.txt | 1615 | Virgin Boy is Selling AT&T Virgin Calling Cards! |
| cards.cap | 33027 | Scythe/KRYN give you New Credit Card Numbers |
| cards1.txt | 14410 | How to Card by The Disk Master (November 21, 1988) |
| cards3.txt | 2466 | If You Don't Know How to Card, This File is For You, by The Serial Killer |
| cardtech.txt | 9033 | Carding, by Bloody Malice |
| cbi-equi.txt | 15178 | Credit Bureau Incorporated and Equifax Credit Information Services, by Kludge (March 29, 1991) |
| cbi-rl | 23705 | CBI General Information Text by Spiritwalker of Renegade Legion |
| cbi.txt | 14615 | Hacking CBI Accounts, by The Ghost of the Panther Modernz |
| cbi4rl.hac | 21842 | CBI General Information Text #4 by SpiritWalker |
| cbiacnt1.txt | 15073 | CBI Account and Merchant Listing, by Video Vindicator |
| cbidoc.hac | 3154 | How to Logon a CBI System, by L.E. Pirate |
| cbiman.txt | 44915 | The Complete CBI Manual of Operations |
| cc-dial.txt | 7244 | Documentation for CC-Dial (Calling Card Dialer Version 1) November 25th, 1993 |
| cc.ing.made.eas | 8102 | Credit Carding Made Easy by David Lightman (March 28, 1985) |
| cc101.txt | 77370 | Credit-Carding 101 Part 1 |
| cc101_2.txt | 10663 | Credit Carding 101 Part 2 |
| cc101_3.txt | 16769 | Credit Carding 101 Part 3 |
| cc101_4.txt | 13990 | Credit Carding 101 Part 4 |
| cc101_5.txt | 12327 | Credit Carding 101 Part 5 |
| cc101_6.txt | 10480 | Credit Carding 101 Part 5 |
| cc_bible.txt | 11627 | The Credit Carding Bible, from BoRRE of MYSTIC |
| ccbanks.hac | 10195 | Credit Card Number Prefixes and the Associated Banks |
| ccc.nfo | 2931 | Youngsters Against McAfee Present Credit Card Commando |
| cccheck.txt | 1448 | DOCUMENTATION: The Calling Card Chekcer by TauTau (1994) |
| cccodes.txt | 3911 | Hacking Credit Card Codes by Omni Kid and The Wyvern |
| ccformat.txt | 2107 | Credit Card Formats, by Shadowmaster of The Power of Plastic (June 14, 1992) |
| ccfraud.txt | 4366 | How to Card Your Ass Off and Never Get Caught |
| ccgenkit.txt | 14336 | Credit Card Number Generation Kit For The Apple by The Phantom Viper |
| ccinfo.txt | 4099 | Credit Card Information by Scooter |
| ccnumber.txt | 1408 | A Collection of Bank Card Formats |
| ccnumberdoc.hac | 2067 | Bank Card Formats |
| ccnus.phk | 1171 | Getting Calling Card Numbers, by the Extortionist |
| ccs.hac | 8049 | Credit Carding Made Easy by David Lightman |
| ccsecrts.txt | 29696 | Calling Card Secrets, from Bell Labs Presented by City Under Seige |
| cctutor.txt | 19237 | A Complete Tutorial on Credit Cards by The Duke of The United Pirating Society |
| cfrd.txt | 16302 | Card Fraud and Computer Evidence (February 14, 1994) |
| citibank.txt | 7057 | Citibank Service Addresses by Dark Helmet (May 21, 1990) |
| ckfraud1.txt | 10692 | Check Fraud Made E-Z by The Raven (August 13, 1992) |
| copier.txt | 10206 | Magentic Stripes, from a variety of sources, typed in by Count Zero of Restricted Data Transmissions |
| crdfraud.txt | 4079 | Credit Card Fraud Made Easy: A Treasure Island Presentation |
| crdtcard.txt | 17968 | Credit Cards for Fun and Profit (August 2, 1984) |
| crdtcarddoc.hac | 17961 | Volume I of The Adventures in Fraud Series by Sneak Thief/Credit Card Fraud Ideas by L.E. Pirate |
| credchk.txt | 1362 | Credit Checks: A Treasure Island Presentation |
| credfrd.txt | 8558 | Credit Card Fraud Ideas!! By L.E. Pirate |
| credguid.txt | 3645 | Credit Card Guide: How to card and not get caught by Cobra Commander of Treasure Island |
| credit | 7688 | Credit Cards for fun and profit! by Southern New York, August, 1984 |
| credit.txt | 3672 | Credit Carding: Here Are Some of the Best Ways |
| credit1.ana | 10622 | Credit Cards I: The Card, by The Administration |
| credit_s.txt | 5116 | Transcription of the Magnetic Data Encoding Standards on some Cards |
| creditca.txt | 17383 | How to Generate Credit Cards by Lost Soulz of Origin |
| creditsc.txt | 3206 | Credit Card Fraud, by Smooth Criminal |
| credscam.txt | 3463 | Credit Card Scams from The New York Safehouse II Elite |
| deacard.txt | 6317 | Beginning to Advanced Carding, by The Avenger of the Data Enforcement Association (January 26, 1991) |
| dosbank.txt | 9871 | DOCUMENTATION: The DOSBank Credit Card Validation Program (1995) |
| fraudcc.txt | 14523 | Protecting the Plastic, by Jack Goldstein of the American Society for Industrial Security (1989) |
| fyd_cc-1.txt | 16568 | The FYD Guide to Card Frauding and its Principles |
| guicardi.txt | 15802 | Carding 101: The Basica, by Dark Grif |
| hackat&t.txt | 2815 | How to Hack AT&T and Get Cards from Them |
| hackincc.txt | 4680 | Hacking Credit Card Codes by Omni-Kid and The Wyvern |
| hackingcdoc.hac | 3531 | Hacking Credit Card Codes by Omni-Kid |
| hacktrw.hac | 2706 | An Experienced Hacker's Guide to Hacking TRW, by Minotaur |
| insidecr.txt | 52141 | Credit Card 101 Part 1: The Players |
| is02card.txt | 10292 | Carding in the 90's by Aeon Flux of Information Society (September 12, 1992) |
| is02cardis.ana | 10467 | Information Society: Carding in the 90's |
| kreditko.txt | 3534 | Basic Credit Card Fraud by Mr. Big of the Swedish Hacking Association (1990) |
| magcard.txt | 72625 | Magnetic Stripe Technology: An Overview |
| magcard2.txt | 16994 | Magentic Card Swipe Reader.. Need Help! |
| makecard.txt | 1359 | Software Documentation: Credit Card Account Number Generator Version 1.0 by Becna |
| merchant.cc | 23292 | Credit Cards and Merchant Numbers |
| metallia.txt | 13545 | Cardinging Volume II by the Metallian |
| minuten.txt | 2201 | Calculate Your Own Minuten Card Numbers, by Martin Fredriksson of MRD (June 10, 1992) |
| narc_7 | 8220 | NARC Infofile 7: Credit Cards |
| nfcardng.txt | 5100 | No-Fail Carding Techniques by Ford Prefect |
| nha-004.txt | 8148 | NetWork Hackers Alliance Issue 4 |
| obtaincards.txt | 7127 | How to obtain Credit Card Numbers and Calling Card Numbers the Easy Way! |
| plastic.txt | 45985 | Card-O-Rama: Magnetic Stripe Technology and Beyond by Count Zero (November 22, 1992) |
| posse1.txt | 17871 | The Art of Cardinb, by the AI Overdose (May 4, 1991) |
| readme.mpi | 2970 | Soft Documentation: Calling Card Calculator v10 by Micropirates |
| ripccn.txt | 4717 | How to Get Credit Cards the Easy Eay by Valaraukar |
| secrets1.hac | 4840 | Big Secrets Volume #1 by The Wyvern: Credit Cards and Lie Detectors |
| shacard.txt | 3615 | Basic Credit Card Fraud, by Mr. Big of Swedish Hacking Association (1990) |
| skip.txt | 13935 | Zen and the Art of Credit Theft |
| tfp-trw.txt | 2589 | Hacking TRW |
| tralia.txt | 5427 | Eline Carding: The Australian Way to Do It! |
| trw-ips.txt | 23735 | The TRW Master File by Infinite Possibilities Society (December 1991) |
| trw.doc | 4048 | General TRW Information by Modem Master |
| trw.hac | 1693 | Quick Notes on getting into TRW |
| trw.txt | 3200 | Information on TRW, by Nitzer Reb |
| trw1.hac | 23129 | Infinite Possibilities Society presents: COMPLETE TRW |
| trw2.hac | 38380 | Infinite Possibilities Society presents: EVEN MORE COMPLETE TRW |
| trwaddrs.txt | 3063 | TRW Address Formats by The Line Breaker (March 1, 1986) |
| trwdef.hac | 7958 | TRW Definitions, by the Line Breaker |
| trwdefs.txt | 6686 | TRW Definitions by The Line Breaker (March 1, 1986) |
| trwdoc.hac | 4278 | General TRW Information, by Modem Master |
| trwguide.hac | 13029 | Renegade Legions Technical Reports: TRW 1.0 |
| trwh.txt | 2499 | Information on TRW, by Nitzer Reb |
| trwinf.hac | 5525 | Several Textfiles about TRW |
| trwinfo.txt | 2760 | General TRW Information by Modem Master |
| trwips.txt | 23935 | The TRW Master File #1 (December 1991) by Infinite Possibilities Society |
| trwtech.hac | 11392 | TRW Terminology: Understanding what you read, by Master Blaster |
| ukccfraud.txt | 5538 | U.K. Credit Card Fraud by Creditman (October 22, 1990) |
| val-amex.txt | 7233 | How to Make Your Own Valid American Express Numbers in One Easy Step, by Saturday Knight |
| valccds.hac | 921 | How you validate Credit Cards |
| visa.txt | 1747 | Calculating Your Own VISA Numbers, by Martin Fredriksson of Sarcastic Existence |
| visahack.txt | 7447 | Some Unchangeable Digits in Visa Credit Cards by Stargazer and Borashi |
| visahackdoc.hac | 7557 | Some Unchangeable Digits in Visa Credit Cards by Stargazer and Borashi |
| vitcard.txt | 7418 | Carding Simplified Part 1: Vital Card Information by Scooter (October 25, 1990) |
| whats.new | 6238 | DOCUMENTATION: CreditMaster Revision History (October 31, 1995) |
| zencredi.ana | 15468 | Zen and the Art of Credit Card Fraud |
| There are 162 files for a total of 1,711,814 bytes. |
It is interesting to note that throughout the 1980's, the vast majorityof busts for hackers came from credit card fraud busts. If you leaf throughsome of the textfiles on this site that mention busts, you will find thatin almost all the files, they mention as an aside that what got the authorities interested in them was some spate of carding. While thelaw was unable to quantify exploration or interaction with computers, the cold transfer of material goods they could understand.
We think it's important for you to understand how we make money. It's pretty simple, actually. The offers for financial products you see on our platform come from companies who pay us. The money we make helps us give you access to free credit scores and reports and helps us create our other great tools and educational materials.
Compensation may factor into how and where products appear on our platform (and in what order). But since we generally make money when you find an offer you like and get, we try to show you offers we think are a good match for you. That's why we provide features like your Approval Odds and savings estimates.
Of course, the offers on our platform don't represent all financial products out there, but our goal is to show you as many great options as we can.
Whenever you hear news about a data breach, you may wonder exactly what hackers can do with your information. As it turns out, quite a lot.
Unfortunately, hackers work fast, too. According to May 2017 research by the Federal Trade Commission, it took only nine minutes before the hackers tried to access the information from a fake data breach.
If you’ve recently found out your data was compromised, then you should know the various ways identity thieves can use your information. This knowledge can prepare you for managing the effects of identity theft as soon as it happens. Adobe cc master collection mac os x crack included megashare.
What is identity theft?
Identity theft is the process of stealing your personal information — like your name, address, Social Security number and email address — and using it without your consent. Identity theft can happen to anyone, and the effects can be more than just an inconvenience.
Hackers may obtain your information in a data breach. But they may also be able to get your information if you enter it on a public computer or go to an unsecured website — and these are just some examples of how hackers can steal your information.
They can then use your personal information in a variety of ways for their own gain and at your expense.
Hack Credit Card On Irc 1031
Here are five ways hackers can take advantage of you and your information:

1. Your info could be used to open credit cards or take out loans
If hackers have your Social Security number, name, birthdate and address, they can open credit cards or apply for loans in your name.
“Hackers obtaining personal information, including Social Security numbers, can enable someone to pose as their victim and get credit or take out loans that they never pay back,” says Steven J.J. Weisman, a lawyer and author of “Identity Theft Alert: 10 Rules You Must Follow to Protect Yourself from America’s #1 Crime“.
2. Hackers can intercept your tax refund
If you’re like most people, you’re excited to get your tax refund. But sadly, hackers can intercept your tax refund by filing a fake tax return, using your Social Security number, birthdate and name.
Consumers who wait until the last minute to file may be more vulnerable. You’d likely only find out once you file your tax return and it gets rejected.
To help prevent this, the IRS recommends the following precautions:
- Always use security software with firewall and anti-virus protections. Use strong passwords.
- Learn to recognize and avoid phishing emails, threatening calls and texts from thieves posing as legitimate organizations such as your bank, credit card companies and even the IRS.
- Don’t click on links or download attachments from unknown or suspicious emails.
- Protect your personal data. Don’t routinely carry your Social Security card, and make sure your tax records are secure.
3. Your info can be used to cover medical treatment
People who steal your info aren’t just using it to buy lavish items. They can also use it to receive medical treatment by using your Social Security number and health insurance account numbers.
“In most cases, (identity thieves) use your same address, phone number… everything. Their goal is to get treatment and/or medications, and then they are gone, leaving very little time for them to be found out,” says Justin Lavelle, chief communications officer at background checking service BeenVerified.com.
In fact, according to research from Michigan State University, there were nearly 1,800 incidents of medical data breaches with patients’ information from October 2009 to December 2016.
Hackers can receive treatments, prescriptions and more by using your benefits. In addition to increased expenses for you, this can also put your own health at risk as the thief’s medical information will now be mixed up with yours.
Hack Credit Card Account Numbers
Be sure to thoroughly review your medical bills and insurance statements as these may show signs of identity theft. You can check if the claim description matches the care you received.
If you see a discrepancy, call your health provider to report it.
Also make a habit of regularly checking your credit reports to check for delinquent (unpaid) medical bills on your credit reports.
4. Hackers can take flight with your airline miles
Using your email and passwords, hackers can get access to your airline miles to book trips or even redeem for cash.
“Airline miles can be converted to cash as easily as going to websites that buy miles,” Lavelle says.
To help prevent this, use a different password than the one you have on other accounts, and keep track of your mile activity regularly.
5. Your info could be used to open utility accounts
According to the Federal Trade Commission (FTC), 13% of fraud incidents in 2016 occurred with phone and utility accounts.
In these cases, hackers may have opened an account with an electric, gas or cellphone company by using a stolen Social Security number. They then can run up tabs on the account, which is under your name, without you knowing.
There’s another scam to be aware of as well. Identity thieves can call you and pretend to be the utility company, threatening to turn off your electricity if you don’t pay up. However, these fraudsters are just trying to steal your money.
If your utility company is asking you to pay up, make sure you’re talking to the real deal and verify your repayment status.
You can do this by checking the utility company’s phone number and also checking your online account to verify your status.
How can you prevent identity theft?
While you can’t prevent a big data breach or ever fully protect yourself against identity theft, there are some measures you can take to make yourself less vulnerable. Here are some quick tips:
- Make sure you have a strong password that has many characters (including a mix of lower- and upper-case letters, numbers and symbols) and has no personally identifiable information or dictionary words.
- When you’re online, make sure the sites you visit are secure. The URL will usually have a lock in the left-hand corner and start with “https”.
- Enable two-factor authentication, so you’ll need to enter a code from your phone to access your accounts.
- Check your financial transactions often, and keep tabs on your credit reports to look for any changes.
Credit Karma has also created another way to help you detect identity theft.
With the ID monitoring feature, you can use your email address to search for any accounts that are in any public data breaches. If your information has been exposed in a breach, we’ll let you know some tips and tools to help you take the right next steps.
We’ll also continue to monitor your credit for free.
What’s next
There’s no shortage of ways hackers can use your information, and they seem to be getting ever more creative.
If you’re a victim of identity theft, you can follow the steps provided by the FTC to help you get through it. You can also submit a complaint through the FTC.
Of course, there are no foolproof methods to preventing identity theft. But taking precautions and catching signs of identity theft as early as possible can help immensely. How bad is smoking crack for your lungs hurt.